Set up SCIM with Azure
This topic walks you through the process of setting up SCIM in Microsoft Azure.
Prerequisites:
Before you begin, you must complete the following prerequisite tasks:
- Set up SSO with Azure. You must configure SSO before you start setting up SCIM.
- Define the groups in Alida to map to your Azure groups.
- Generate an authentication token. Ensure
that you have access to the following settings from the Alida
User Auto-Provisioning page:
- Base URL: The Alida SCIM API endpoint URL.
- Token: The API token for authentication with the Alida SCIM API endpoints.
Important: Users will not be able to sign in to Alida while
the initial provisioning process is running. Plan your user auto-provisioning
roll-out at a time that minimizes user impact.
- Log in to the Azure Portal at https://portal.azure.com.
- Under Azure services, click Enterprise applications.
- Click the name of the SSO application you created for Alida.
- Select in the left menu.
-
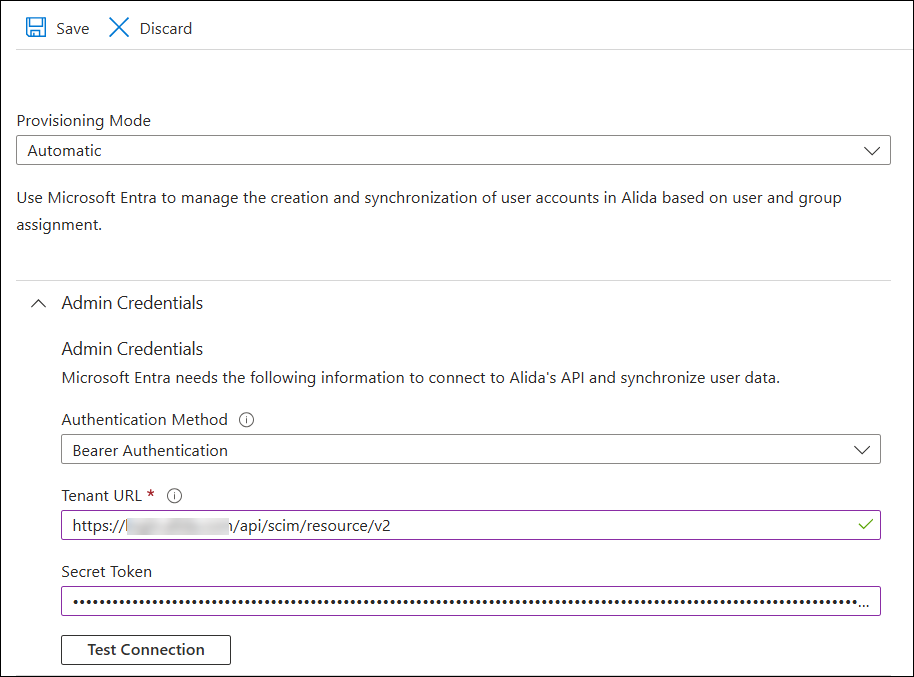
Configure your authentication credentials for connecting to the
Alida SCIM API:
-
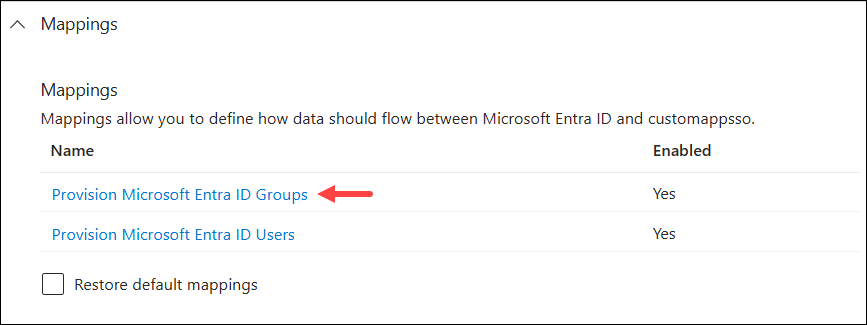
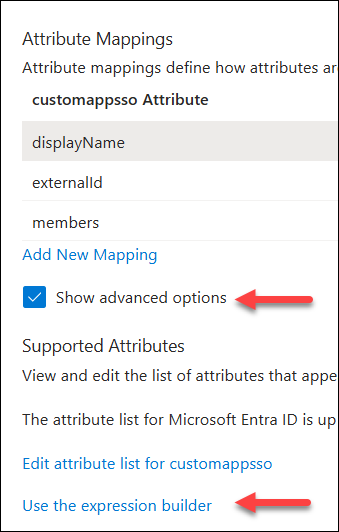
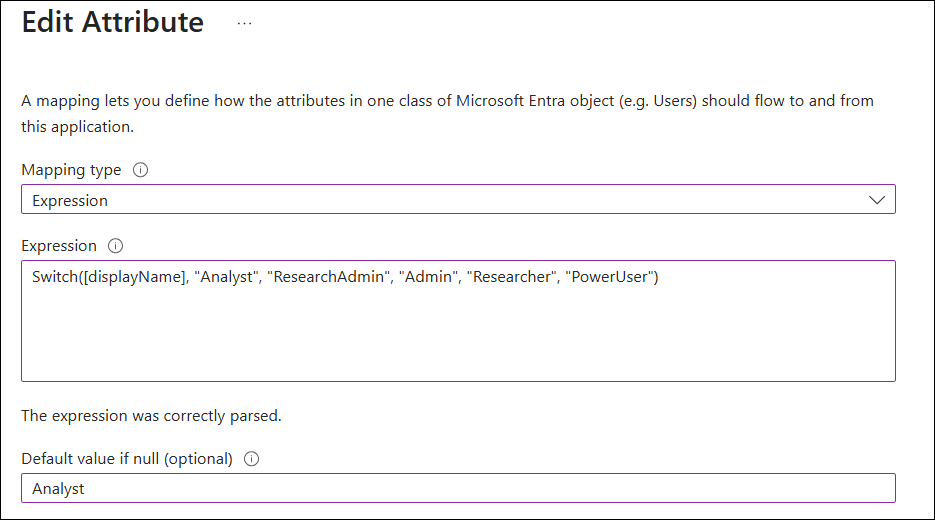
Configure attribute mappings to define how attributes are
synchronized between Microsoft Entra ID and Alida:
-
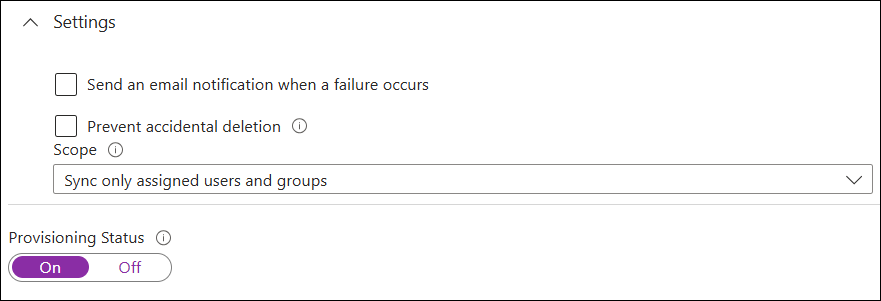
Turn on provisioning:
Provisioning will
begin. The initial cycle can take some time depending on the number of users
assigned.