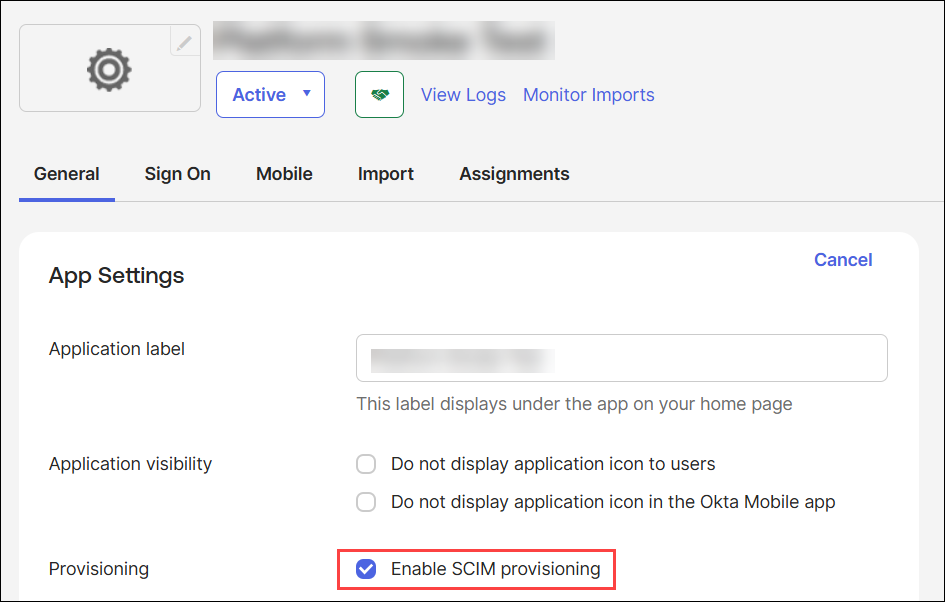
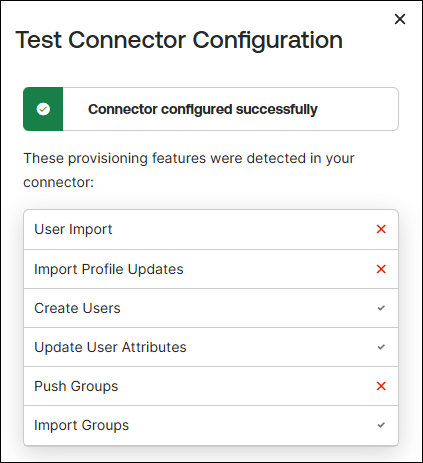
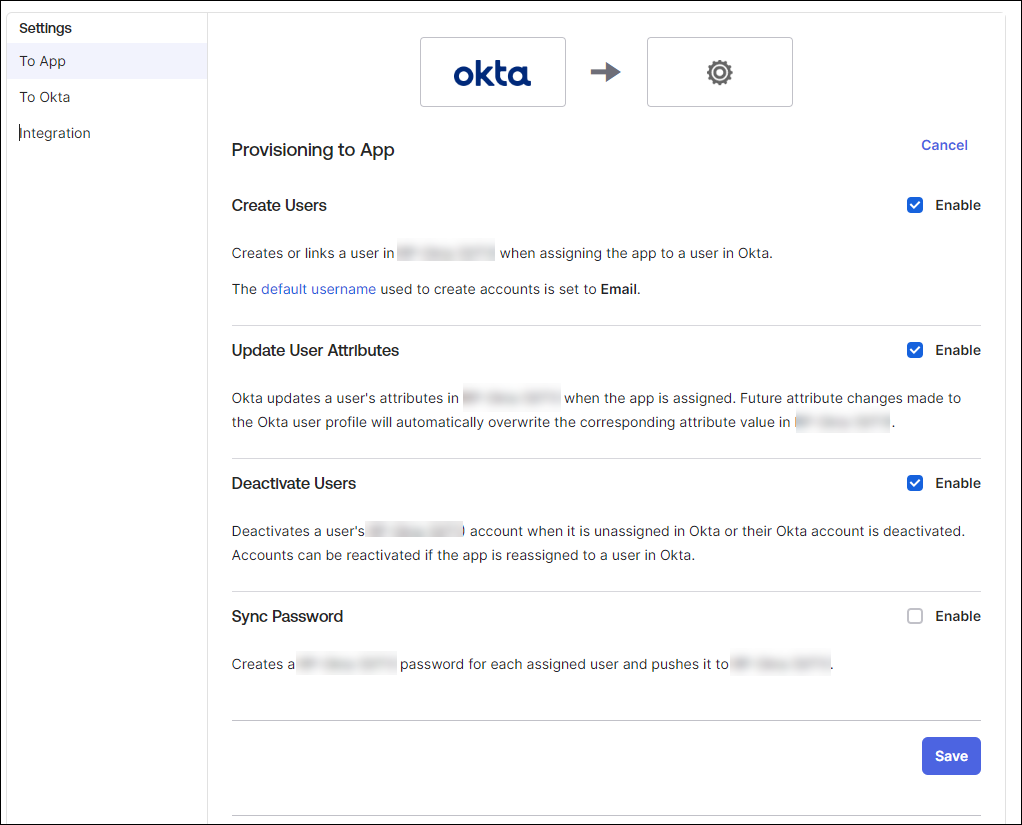
Set up SCIM with Okta
This topic walks you through the process of setting up SCIM in Okta.
Prerequisites:
Before you begin, you must complete the following prerequisite tasks:
- Set up SSO with Okta. You must configure SSO before you start setting up SCIM.
- Define the groups in Alida to map to your Azure groups.
- Generate an authentication token. Ensure
that you have access to the following settings from the Alida
User Auto-Provisioning page:
- Base URL: The Alida SCIM API endpoint URL.
- Token: The API token for authentication with the Alida SCIM API endpoints.
Important: Users will not be able to sign in to Alida while
the initial provisioning process is running. Plan your user auto-provisioning
roll-out at a time that minimizes user impact.